The landscape of Cyber Security is constantly changing. Cyber-criminals, black-hat hackers and bad-actors are trying to access and steal what doesn’t belong to them, but they can be stopped. Robust Information Security processes and regular penetration testing can help identify potential vulnerabilities and help prevent them from being exploited. Preventing breaches of immeasurable potential tomorrow is within your power. By taking action today, you can safeguard your organization and the valuable assets and information it holds. Don’t wait until it’s too late! Take the first step now to protect yourself and your business from the devastating consequences of a breach by arranging a security assessment with System Secure. Application Testing – Security testing for applications that anyone might access through a web browser or mobile device, etc. Infrastructure Testing – Scanning IP addresses for open ports, and testing for vulnerabilities caused by lack of patching or by configuration flaws. Adversary Simulation & Red Teaming – A simulated real world cyber attack to pursue particular goals and to test the response time and effectiveness of a security operations centre. Phishing & Social Engineering – Targeting the users, rather than the systems to test security policies and identify unconventional vulnerabilities. This service includes awareness training as well as simulation. Managed Service Provider Training, Support & Security Consultancy – Not all security assessments fit into a particular box/service line. System Secure can offer bespoke security assessments to meet the needs of our clients.Test, Identify, Remediate
Cyber Security Consultancy and Penetration Testing Services:
How we work at System Secure
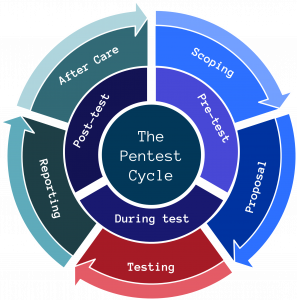
We are a pragmatic security consultancy that works around your needs:
- We work with you to understand your business, technology and the scope of your requirements.
- We document the recommended specifications for an engagement in a formal proposal.
- We perform penetration testing activities in line with the agreed proposal.
- We clearly document our findings, with additional remediation advice.
- After the test, we will continue to work with you for advice, guidance and support.
Black Box, Grey Box or White Box
There are three main categories of software testing: black box, grey box and white box. Each method has its own advantages and disadvantages:
- Black box testing is a simulation of a real life scenario where no privileged access is provided. The tester is given no information about the inner workings of the application. This type of testing is useful for finding threats and bugs which affect all users equally. Also for finding issues with a program that cannot be fixed by changes to its source code; such as configuration problems.
- Grey box testing is similar to black box testing, but where we are provided with test user accounts and allows testers access to some information about how the application works. This may include things like documentation, specifications and design documents in order to test more thoroughly.
- White box testing is similar to grey box testing though provides testers with full knowledge of how the application works, including its source code and additional design documentation where required. This is a very thorough form of testing and is the most ideal method to ensure a thorough test.
Human Vulnerabilities, Phishing and Social Engineering.
What about human vulnerabilities?
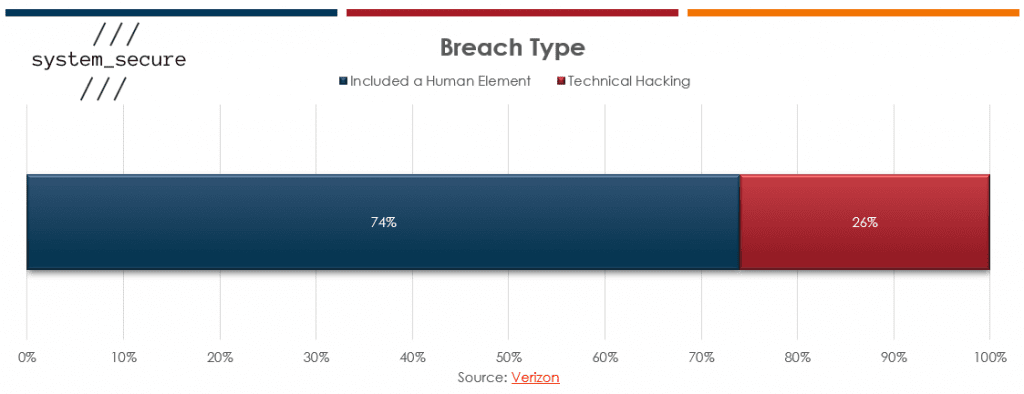
Nearly ¾ of all breaches have a human element as part of the attack. Our phishing_secure programme strives to fight against social engineering based threats by combining:
- Meaningful and “Affective” Training
- Phishing Simulation
- Intelligence Updates