 Infrastructure testing is key to ensure your organisation’s networks and services are protected. We can assess the security of any type of IT infrastructure. We most commonly deal with the following broad categories:
Infrastructure testing is key to ensure your organisation’s networks and services are protected. We can assess the security of any type of IT infrastructure. We most commonly deal with the following broad categories:
- Network infrastructure
- Cloud platform infrastructure
- Internet of Thing (IoT) devices and platforms
- Breakout testing
- Configuration review
Enquire about Infrastructure Testing
Get in touch to find out more or to arrange a scoping call.
What is Infrastructure Penetration Testing?
Infrastructure Penetration Testing involves simulating real-world cyberattacks to identify vulnerabilities, weaknesses, and potential entry points that malicious actors could exploit. Our experts at System Secure uncover these issues and advise on how to proactively strengthen your security measures, reduce the risk of security breaches, and ensure compliance with industry regulations.
Our penetration testing services are tailored to support any required compliance framework, including:
- ISO 27001 – control objective A12.6
- IATF 16949 section 6.1.2.3 Contingency Plans
- Telecommunications Security Act (TSA) – section 105A
- General Data Protection Regulation (GDPR) – Article 32.1d
Infrastructure penetration testing specifically aims to identify and help address security vulnerabilities that might be present on network infrastructure. This includes servers, workstations, and networking equipment such as routers, firewalls, and switches. Infrastructure penetration testing targets network IP addresses whether external/Internet-facing, or internal addresses on private network such as an office or datacentre. Testing activities aim to identify active services exposed on the target IP addresses and assess those services for any potential risks they might introduce.
Internal Infrastructure Testing
Internal infrastructure is a key component in determining the overall security posture of an organisation. Users and internal systems are typically assumed to be trusted and are more likely to have access to sensitive information or privileged functionality. While internal staff may well be trustworthy, their workstations and user accounts may be compromised by a malicious actor and leveraged for their own purposes. As such, it is crucial to determine the security posture of services and systems within the internal estate.
External Infrastructure Testing
Externally facing infrastructure is a ripe target for Internet-based threat actors. This infrastructure should be regularly tested to identify any external services that are susceptible to compromise. Any security risks that are identified can then be remediated before they are exploited by malicious threat actors.
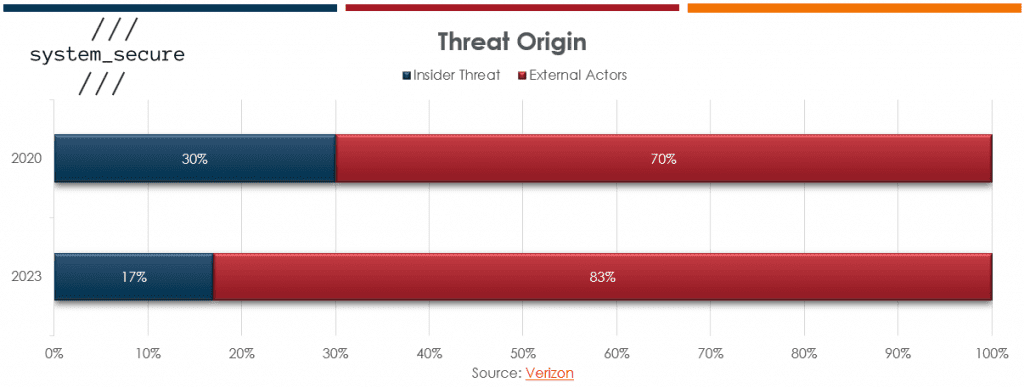
Testing from both internal and external perspectives is vital. Not all threats come from external actors; sometimes someone on the inside of an organisation can be the threat. Although an unpleasant thought; a member of staff might have a vengeful or financial motive to cause deliberate harm to an organisation. That being said, it is much more likely that someone on the inside makes a mistake or causes an incident through simple negligence. Thorough infrastructure testing will highlight any risks from insiders and help prevent them, regardless of motive.
Infrastructure Testing
Infrastructure testing is an important part of any security assessment. It helps us identify vulnerabilities in your network infrastructure and systems, such as servers, routers, switches and other devices that are used to manage your IT environment. This can include wireless access points, firewalls, load balancers or any equipment that helps facilitate the operation of a network.
This normally involves testing servers and network devices from a network-perspective. We scan IP addresses as the targets, looking for any open TCP/UDP ports that expose services to the network. We then look for any vulnerabilities in those services that were either introduced by lack of patching or by configuration flaws. These could either be Internet IP addresses, or internal networks accessed by being physically on-site or via VPN.
This can also be approached in the Black, Grey or White box testing manner. Most commonly we would recommend Grey box testing for internal networks, where we would request that we are provided with domain user account(s) in order to test more thoroughly and efficiently; ideally a Domain Admin account.
Cloud Platform Testing
Most clients now host their applications and sometimes their entire infrastructure on a cloud platform such as AWS/GCP/Azure. Primarily for cost reasons as well as scalability and security, offloading the responsibility for tasks such as patching to the cloud provider.
These are large, complex environments which means it’s definitely possible to introduce security vulnerabilities through misconfigurations. This service aims to initially identify any vulnerabilities but also educate the client on how to identify and prevent these vulnerabilities in future through using the in-built scanning tools that often come packaged with these platforms.
IoT Device / Platform Testing
More and more devices are Internet-connected nowadays, exposing them to potential compromise by remote attackers.
Traditionally devices like Routers and Network-Attached Storage (NAS) devices would be tested. As technology advances, an infrastructure could include anything from IP cameras, POS terminals, smart meters, EV chargers, smart heating systems, etc.
We can test these, both from a software and a hardware perspective. Software testing would involved assessing the operating system running on the device and any applications running. Hardware testing might include seeing whether the physical device can be tampered with in order to perform malicious actions or gain access to sensitive data.
Breakout Testing
Some clients rely on restricted desktop environments whereby only a subset of applications and functionality are meant to be exposed. This could be using software like Citrix. This could also be something like a kiosk exposed to the public.
The aim of this testing is to try and identify ways to break out of the restricted environment and gain access to unwanted functionality such as cmd/PowerShell or other sensitive data on the filesystem.
Configuration Review
In many cases we can assess the security of a system or product by reviewing its configuration, rather than active testing of a live device. This might simply be reviewing a firewall or router configuration file. Alternatively, performing a build review of a server or workstation or assessing the security of a wireless access point’s configuration.