The Phishing Secure Programme
Phishing and Social Engineering are the most common attack vectors for hackers, cyber criminals, hacktivists, and state sponsored hacker groups.
In 2023, Verizon noted that 74% of all recorded breaches included a human element, though some kind of social engineering. In response, our experts at System Secure have developed the phishing_secure programme to help to combat socially engineered breaches.
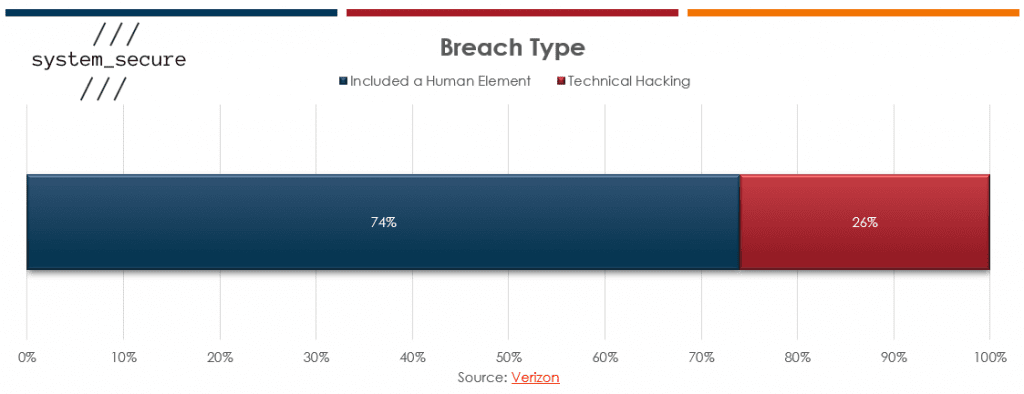
74% of recorded breaches in 2023 included a human aspect; such as phishing or negligence.
Penetration Testing fights against technical hacking, and reduces the impact of future breaches. To fight against social engineering a different approach is needed.
Our phishing_secure programme combines meaningful and empathetic training and updates with phishing simulation exercises.
To truly equip your staff to combat phishing and other forms of social engineering, we use a three part method:
- Training – to teach users to recognise social engineering, to validate authenticity, and address potential threats
- Phishing Simulation – to assess the users ability to recognise and validate an attempted scam
- Intelligence updates – to inform of current examples of scams and attacks; in short, shareable snippets
Of course, the overall aim is to prevent breaches from occurring through social engineering techniques. We excel at this because we embed these key objectives into each element:
- Acknowledge that anyone can be scammed, it is not a source of shame
- Appreciate that everyone can be trained and deserves the protection that knowledge brings
- Equip all who will listen, with definitive ways to recognise, validate and prevent attempts at social engineering
- Encourage others to support and hold each other to account to prevent further scams
Phishing Secure options:
The Phishing Secure programme is open to all Managed Service Providers and IT departments working on behalf of a wider organisation.
| Service | Silver (free) | Gold (subscription) |
|---|---|---|
| Intelligence updates | Monthly | Monthly |
| In-person training | Sold separately | Expenses only |
| Virtual training | Up to 10 users | 1 per user, per year |
| Topical Phishing Simulation | Sold separately | Quarterly |
| Bespoke Phishing Simulation | Sold separately | Discounted |
| E-learning* | Via System Secure | LMS content available |
*E-learning content is being refreshed for 2024
What is involved in the Phishing Secure programme
The phishing_secure programme is designed to combat all forms of social engineering. We accomplish this through degrees of training, phishing simulations and intelligence updates.
What is “Social Engineering”
Verb Cybersecurity
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme. – Wikipedia
- Examples of Social Engineering include; Phishing, Spear Phishing, Whaling, Vishing, Smishing, Qishing, Website Spoofing, conversation manipulation, and even mentalism, etc.
Phishing Simulations
Simulated Phishing attacks have long been part of our arsenal of services. A phishing simulation is the only real way to assess the workforce’s level of understanding and preparedness.
The primary aim of the phishing simulation is that the user understands what to do in the event of a suspected scam. With this in mind, any user that falls for our phishing simulations will be treated sensitively. They will be directed to a page that encourages them not to worry, but signposts them to additional training and support.
As part of all phishing simulations, we will report on:
- Malicious links clicked
- Credentials and data obtained
- Harmful files downloaded
- Specific users recommended for additional training and support.
As part of our phishing_secure programme we offer two phishing simulation options:
Quarterly Topical Phishing
Every quarter we build a new simulated scam using a combination of steps. We build these using GoPhish, and base the attack on themes or methods that are trending at the time. Any user assigned to this service will be hit with at least one general phishing or other social engineering attack.
This is an ideal service for IT managers for professionals in any industry where an awareness of cyber security is beneficial. IT managers will receive a quarterly report for their users to act upon as they will.
Bespoke Spear Phishing
For organisations that require something a little more deliberate and impactful, we can offer our bespoke spear phishing service. This differs to the topical Phishing simulation, in that this will be more targeted. This simulation involves elements of impersonation and spoofing to make the scam seem more realistic and replicate what a determined threat actor would do in real life.
This service is ideal for organisations where personnel have access to high risk or large valoumes of data. This service can also be tailored to high level employees, such as C-suite executives.
Intelligence updates
 Our experts are constantly picking up on new scams and attacks through various channels. We aim to curate these into our updated training packages, but for phishing_secure partners we collate a monthly email update of important scams and breaches to be aware of. This information in boiled down into short bitesize chunks that can easily be added into newsletters and social media updates. This will include common attack types, new methods or types of requests, as well as new methods of defence.
Our experts are constantly picking up on new scams and attacks through various channels. We aim to curate these into our updated training packages, but for phishing_secure partners we collate a monthly email update of important scams and breaches to be aware of. This information in boiled down into short bitesize chunks that can easily be added into newsletters and social media updates. This will include common attack types, new methods or types of requests, as well as new methods of defence.
Partners can choose for any number of email addresses to be added to this list – strictly for updates only. We are happy to provide this information to our partners to be shared and used as you see fit. After all, protecting and supporting our customers is both your and our highest priority.
Phishing Secure training programme
Our training package has been built to be dynamic, engaging and most importantly effective at moving people to act. Our training is updated with current examples of breaches and relatable scams. Organisation that require annual refresher training can guarantee a unique and current experience every time.
We recommend all IT users and professionals at any level take part in our live classroom training. We recognise that this is not always possible so other options are available and we happily consider custom packages.
Each of the below options features the following learning objectives:
- Learners will recognise the different common types of cyber security threat that might target them.
- Learners will review examples of phishing emails and different methods of social engineering.
- Learners will propose how to respond to or prevent a suspected scam or phishing attack.
- Learners explore good practice in relation to secure IT user behaviour and put measures in place to defend against cyber security threats.
In-person classroom training – 90-105 minutes
This is the best and most highly praised training offering. There is no substitute for in-person training; being accountable to a trainer and other colleagues. These live session allow for discussion about current issues, and allowing space to ask difficult questions. Each session include practical activities, examples demonstrating “how to create an effective scam” and exercises to improve an individuals security posture at work and with their personal devices.
The key to a good training session, is to reach each attendee on an affective level, as well as intellectually.
These can be facilitated in any UK company premises or venue, with up to 4 sessions per day per trainer.
“[The training] was very engaging and the information easy to understand, particularly as we work in a very confidential environment and also typically have less ‘techy’ staff. The delivery was fun, with lots of laughter, and [our trainer] was clearly passionate about phishing awareness and protecting individuals/organisations. The real life examples were really helpful, as well as practical tips for improving our security” – Lauren
Live virtual classroom training – 75-90 minutes
We replicate our in-person classes in virtual classrooms as closely as we can to facilitate those that cannot be there in person. Additional resources are provided to enable each attendee to practice the exercises that will improve their own security.
These sessions can be facilitated at the customers convenience.
“The webinars have been really good, full of information that I can use in my work. The tutors are friendly and easy to talk to, they make the sessions fun and they are more than willing to help you in any way they can. The [phishing training] webinar with [trainer] was very useful, he gave us loads of brilliant information and links to so many things that we can use.” – Ellie
E-learning package – 30-45 minutes
For organisations requiring regularly refresher training and certification we also offer a “Phishing and Cyber Security Awareness” e-learning package. This can be purchased and embedded into any Learning Management System, or can be completed directly through System Secure.
VERY IMPORTANT – E-learning is no substitute for real life training! No matter how much as we want to sell this product. No matter how well we think we made it. It is important to acknowledge e-learning does not work for most people. Many e-learning customers simply go through the motions of clicking ‘next’, just to get to the end, beat the quiz and claim a certificate… learning very little.
This is because their affective domain has not been triggered. Why is this important? Because ALL scams rely on triggering the affective domain. Emotions are required to make scams successful, therefore recognition and control of the right emotions are the key to make the training successful.
In short – if scams use emotions, scam prevention must include emotions.
Enquire about the phishing_secure programme
Get in touch to find out more about our phishing_secure programme.
